Imagine sipping your morning latte in a bustling airport café, laptop open, emails pinging…yet every keystroke might be seen by cybercriminals lurking on the same network.
Public WiFi feels like a gift—until it becomes a hacker’s runway. In this guide, you’ll discover how to lock down your connection with proven VPN setups, browser tweaks, and two-factor authentication.
You’ll also learn emergency backups—from travel routers to power-bank hotspots—and spot malicious networks before they do harm.
Whether you’re a business traveler, digital nomad, or weekend adventurer, these actionable steps ensure that “free” WiFi never costs you peace of mind.
Understanding Public WiFi Threats
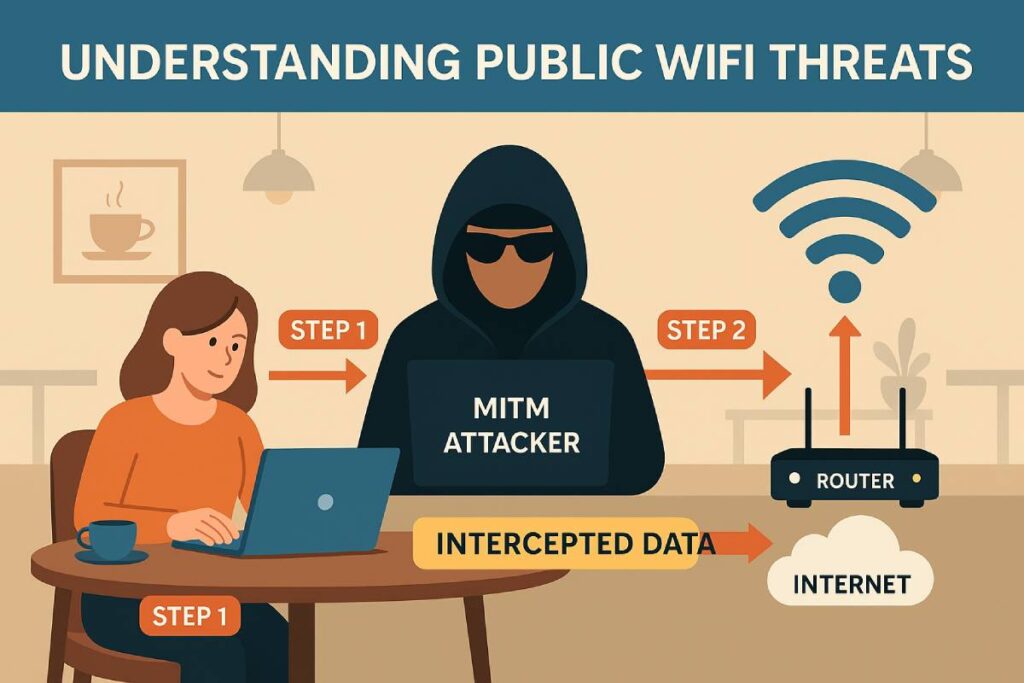
When you’re traveling and tethered to a café or airport lounge network, free WiFi can feel like a gift—until it becomes a gateway for cybercriminals. Unsecured public hotspots expose you to a range of attacks that can compromise credentials, banking sessions, and personal data. Below, we break down the three most prevalent threats and then illustrate their real-world impact through a café hack that cost a freelancer $2,000.
Common Attack Types
| Attack Type | What It Is | Estimated Incidence |
|---|---|---|
| Man-in-the-Middle (MITM) Attacks | A hacker secretly intercepts and relays communications between your device and the WiFi router, capturing login credentials or financial data | Represent 19 % of all successful cyber-attacks |
| Rogue Hotspots (Evil Twins) | Fake WiFi networks set up to mimic legitimate ones; once you join, the attacker can harvest everything you send | 94 % of public WiFi networks are vulnerable to evil-twin exploits |
| Packet Sniffing & Eavesdropping | Tools capture unencrypted data packets as they flow over the network, letting attackers read emails, passwords, and more | 43 % of free-WiFi users report data compromise on unsecured networks |
Real-World Case Study
A café-hacking incident that cost a freelancer $2,000
A freelance graphic designer connected to “CityCafe_WiFi” to meet a deadline. Unbeknownst to her, an attacker had deployed a rogue hotspot named “CityCafe_Free” with a stronger signal. Within minutes, the attacker used packet-sniffing tools to steal her session cookies and banking credentials. By the time her bank’s fraud alerts kicked in, ~$2,000 had been siphoned from her account. She faced a multi-day dispute and recovery process to reclaim her funds.
Key Lessons Learned
- Verify Network Authenticity: Always confirm the exact SSID with staff or signage; avoid networks with similar or generic names.
- Use a VPN: Encrypt all your traffic through a reputable VPN with a kill-switch feature to block any leaks if the connection drops.
- Enable Two-Factor Authentication: Add a second layer of security on banking and email accounts to prevent unauthorized logins, even if credentials are stolen.
- Limit Sensitive Activities: Postpone online banking, shopping, or any login that involves personal data until you’re on a trusted or private network.
- Monitor Alerts & Act Fast: Set up instant fraud notifications on your bank and credit cards; rapid response can cap your losses.
Pre-Travel Security Checklist
Before you even lace up your hiking boots, make sure your digital gear is locked down. Follow this checklist to patch up vulnerabilities, strengthen credentials, and arm your browser—so that free WiFi never feels risky again.
Downloadable WiFi Safety Checklist
👉 CTA: Get Your Free WiFi Safety Checklist
A printable PDF covering every pre-travel step—from installing a VPN to enabling browser privacy settings. Perfect for carry-on or inbox reference.
Keep Software Updated & Use Strong Passwords
- Why it matters: Unpatched software is a hacker’s playground—60 % of data breaches exploit known vulnerabilities that had patches available but weren’t applied.
- Action steps:
- Enable automatic updates on your operating system and all travel-critical apps (email, messaging, banking).
- Audit installed software: Remove unused programs to minimize your attack surface.
- Create strong, unique passwords: Aim for 12+ characters with a mix of letters, numbers, and symbols.
Choose the Right VPN & Password Manager
- VPN on public WiFi: Only about one-third of users deploy a VPN when connecting to free hotspots—yet encrypting your tunnel stops eavesdroppers in their tracks.
- Password managers: Despite experts’ advice, 46 % of people have never used one—leaving nearly half of travelers juggling weak or reused passwords.
- Quick comparison:
| Tool Category | Free Option | Paid Upgrade |
|---|---|---|
| VPN | Proton VPN Free | ExpressVPN |
| Password Manager | Bitwarden Free | 1Password |
Tip: Look for VPNs with a kill-switch and no-logs policy, plus password managers offering browser extensions and secure vault syncing.
Pre-Install Privacy Browser Extensions
- Ad & tracker blocking: Almost one-third (31.5 %) of internet users now run ad-blockers or privacy extensions—these tools also stop invisible trackers on public WiFi.
- Must-have addons:
- HTTPS-Only (forces encrypted connections)
- uBlock Origin or Privacy Badger (blocks ads & trackers)
- NoScript or ScriptSafe (lets you whitelist trusted sites)
By completing these four steps—downloading your PDF checklist, updating software, choosing robust VPN/password tools, and locking down your browser—you’ll dramatically reduce your risk on any public network. Ready for takeoff? Your data safety starts before you even leave home.
Step-by-Step Guide: Securing Your Connection
Follow these practical steps—backed by real statistics—to lock down your data on any free hotspot.
Install & Configure a VPN
- Why a VPN? Only 40 % of users deploy a VPN on public WiFi, leaving the majority exposed to packet sniffers and rogue hotspots.
- Key features for travelers:
- No-logs policy: Ensures your browsing history and metadata aren’t stored or shared.
- Kill switch: Automatically severs your connection if the VPN drops, preventing unencrypted fallback.
- AES-256 encryption: Industry-standard cipher to thwart eavesdroppers.
- Wide server network: Allows you to switch regions for speed, reliability, and geo-unblocking.
- Adoption rates: About 31 % of global internet users have a VPN installed—yet only one-third use it specifically on public hotspots.
- Setup differences: PlatformApp InstallationKill-Switch SupportiOS/AndroidDownload from App Store or Play Store; tap to connectAvailable in most premium appsWindows/macOSInstall desktop client; choose server & enable optionsBuilt into app settings
Harden Your Browser
- Enforce HTTPS-Only Mode: With 98 % of human-generated traffic now encrypted via HTTPS, forcing HTTPS prevents downgrades to insecure HTTP connections.
- Ad & tracker blocking: Over 31 % of users run ad-blockers or privacy extensions, which also stop hidden trackers on public networks.
- Recommended extensions:
- HTTPS Everywhere (auto-upgrades HTTP → HTTPS)
- uBlock Origin or Privacy Badger (blocks ads & invisible trackers)
- NoScript (whitelists trusted scripts only)
- Recommended extensions:
- Disable Auto-Join Networks: Turn off “auto-connect” to prevent your device from jumping onto malicious “evil twin” hotspots without your knowledge.
Enable Two-Factor Authentication
- Why 2FA? Enabling multi-factor authentication can block over 99.9 % of automated account-takeover attacks. Yet only 45 % of internet users have turned it on for at least one account.
- Which accounts first? Prioritize email, banking, and your VPN login—these serve as keys to everything else.
- SMS vs. Authenticator Apps: AttributeSMS-Based 2FAAuthenticator AppSetup ComplexityVery easy (just enter phone number)Moderate (install & register app) Security LevelLow (vulnerable to SIM-swap & interception) High (TOTP codes, phishing-resistant)Offline AvailabilityYes (receives SMS)Yes (generates codes without internet)Phishing ResistanceLowHigh
By following these three core steps—installing a robust VPN, hardening your browser, and enabling 2FA—you’ll transform any public hotspot into a secure online environment. Next up: exploring backup connectivity options and additional tools to stay safe on the go!
Alternative Connectivity Options
When public WiFi isn’t trustworthy or available, these alternative methods keep you online without sacrificing security or budget.
Using Mobile Hotspots Safely
Tethering Best Practices
- Limit shared devices: Only connect devices you absolutely need—every extra gadget increases attack surface.
- Set a strong hotspot password: Use a unique, 12-character minimum passphrase (letters, numbers, symbols).
- Use WPA3 if available: WPA3 is the latest WiFi security protocol and prevents brute-force attacks.
- Monitor connected devices: Check your phone’s hotspot settings and kick off any unknown connections.
- Turn off when idle: Disable tethering immediately when you’re done—no “always-on” hotspots.
Why it matters: 81 % of travelers say internet access is essential or very important when choosing accommodations—your phone’s hotspot can fill gaps where public WiFi fails.
Data-Plan Recommendations
Choose a plan that balances cost, speed, and duration. Below are representative unlimited 4G/LTE travel eSIM plans (no throttling) from Holafly:
| Duration | Price (USD) | Validity |
|---|---|---|
| 5 days | $19 | 5 days |
| 10 days | $34 | 10 days |
| 15 days | $47 | 15 days |
| 20 days | $54 | 20 days |
| 30 days | $64 | 30 days |
| 60 days | $84 | 60 days |
| 90 days | $99 | 90 days |
(Unlimited data; speeds capped at 4G/LTE)
Pro tip: If you plan to share tethering across multiple devices, opt for a plan of at least 10 GB/day equivalent to avoid slowdowns under network congestion.
Spotting & Avoiding Unsafe Networks
When it comes to public WiFi, the first line of defense is simply recognizing a malicious hotspot before you connect. Below is a quick-reference sidebar to flag suspicious networks—and three expert-tested strategies to stay one step ahead of hackers.
Checklist Sidebar: “5 Warning Signs of a Malicious Hotspot”
| Warning Sign | Why It’s Suspicious |
|---|---|
| Generic SSID (e.g., “Free_WiFi”) | Lacks any unique identifier—attackers often choose broad names to lure everyone. |
| Duplicate or Altered Name | Minor tweaks to a known network (e.g., “HotelWiFi” → “Ht̶e̶lWiFi”) are telltale “evil twin” traps. |
| No Password or Captive Portal | Legitimate venues at least require a tap-through; fully open networks are rare for reputable businesses. |
| Overly Intrusive Login | Portals asking for personal details (full name, passport number, phone) go beyond standard “accept terms” pages. |
| Unencrypted Connection (HTTP) | If your browser warns “Not secure” or fails to auto-upgrade to HTTPS, data travels in clear text. |
Verifying SSIDs & Asking Staff
- Confirm the exact network name.
- Attackers exploit convenience: 40 % of users choose hotspots based on name similarity alone.
- Always glance at official signage or ask a barista/desk clerk for the exact SSID to avoid impostors.
- Disable auto-join.
- Over 63 % of daily public-WiFi users auto-connect to the strongest or previously used network—making one mistake repeat itself.
- Turn off “auto-join” in your device’s WiFi settings so you pick networks consciously.
Avoiding Captive-Portal Traps
- Watch for unexpected login screens.
Legitimate venues typically use simple “Accept terms” portals. If you’re asked for email verification codes, phone numbers, or overly personal info, hit “Cancel” and verify with staff. - Check the portal URL and certificate.
- Look for “https://” and a lock icon in the browser bar before entering any credentials.
- Malicious captive portals sometimes use unsecured HTTP pages or mismatched domain names.
Case Study: How a Student Traveler Detected a Fake Network
Scenario:
Anna, a journalism student in Lisbon, needed WiFi to file her article. Her phone listed two options: “LisbonCentral” and “LisbonCentral_Guest”. The “Guest” network asked for her university email, department, and student ID—more than any café had ever required.
What She Did:
- Paused and compared. She recalled the official SSID was “LisbonCentral” (not “_Guest”).
- Asked a barista. They confirmed only “LisbonCentral” was valid—and that they’d never collect student IDs.
- Ignored the fake network. She connected to the genuine WiFi, activated her VPN, and filed her report securely.
Lessons Learned:
- Rogue hotspots prey on minor variations in names—always double-check.
- Overreaching captive portals are a red flag; legitimate providers rarely ask for extra personal details.
- A quick staff query saves you hours of identity-theft headaches.
By mastering these spotting techniques—backed by real data—you’ll sidestep malicious hotspots and keep your personal information under lock and key on every journey.
Emergency Backup Strategies
When your primary connection falters, these backup options keep you online—and safe—no matter where you roam.
Portable Travel Routers with Built-in VPN
Hardware routers with integrated VPN turn any wired or wireless source into a private, encrypted network—ideal when public hotspots fail.
- Rising adoption: In Cybernews’s “Best Portable Wi-Fi Routers for Travel in 2025,” 4 of the top 6 models (≈67 %) feature built-in OpenVPN/WireGuard support, underscoring travelers’ demand for on-device encryption over software-only VPN apps.
- Serverless security: Devices like the Deeper Connect Air use a decentralized private network (DPN) to avoid single-point-of-failure servers, offering military-grade encryption and ad-blocking—trusted by frequent flyers for stable performance.
| Device | VPN Protocols | Max Speed | Max Devices | Price |
|---|---|---|---|---|
| TP-Link AX1500 (TL-WR1502X) | OpenVPN, WireGuard | 1.5 Gbps | Up to 15 devices | $49.99 |
| GL.iNet Beryl AX (GL-MT3000) | OpenVPN, WireGuard | 3 Gbps | Unlimited | $86.90 |
| GL.iNet Mango (GL-MT300N-V2) | OpenVPN, WireGuard | 300 Mbps | Up to 10 devices | $26.91 |
| Deeper Connect Air | Serverless DPN | 300 Mbps | Up to 5 devices | $149.97 |
Power-Bank + Mobile-Hotspot Combos
When you need both juice and connectivity, hybrid devices deliver.
- All-in-one convenience: The Solis Go pairs an 8,000 mAh power bank (≈48 hours runtime) with a global LTE hotspot—no local SIM required—covering 140+ countries and up to 10 devices for $129.00.
- Perfect for off-grid days: Charge your phone, tether laptops, and never hunt for an outlet.
| Device | Battery | Coverage | Max Devices | Price |
|---|---|---|---|---|
| Solis Go Hotspot & Power Bank | 8,000 mAh (48 h) | 140+ countries | Up to 10 | $129.00 |
Local Café Loyalty Programs for Vetted Networks
Some cafés gatekeep their Wi-Fi through loyalty sign-ups, balancing security with marketing benefits.
- Loyalty-driven vetting: By requiring an email or phone number, venues deter casual hackers while growing their CRM.
- Proven lift: Research from PW Consulting shows properties using captive-portal loyalty enrollment achieve 29 % higher sign-ups than traditional methods.
- Better conversions: Visits-to-contact conversion rates of 2–5 % on optimized portals far exceed the < 1 % typical for “just click to connect” networks.
| Metric | Captive-Portal Loyalty | Traditional Open Wi-Fi |
|---|---|---|
| Enrollment Rate | +29 % over baseline | 100 % baseline |
| Visits-to-contact Conversion | 2 %–5 % | < 1 % |
With these emergency strategies—dedicated VPN routers, combo hotspots, and vetted café networks—you’ll always have a secure lane to the internet, even when public Wi-Fi lets you down.
Top Tools & App Recommendations
To fortify your “always-on-the-go” setup, here are my go-to tools—each vetted for security, reliability, and ease of use.
- VPN: A Virtual Private Network is non-negotiable on public WiFi. In fact, 31 % of global internet users now rely on VPNs to encrypt their connections and block eavesdroppers.
- Password Manager: With password reuse driving over half of breaches, only 30 % of internet users have adopted a password manager—leaving many travelers at unnecessary risk.
- Browser Security:
- uBlock Origin blocks ads and invisible trackers, and today 31.5 % of internet users run ad blockers at least sometimes to protect their privacy.
- HTTPS Everywhere forces encrypted connections on sites, critical given that 87.9 % of websites already default to HTTPS—but some still slip into HTTP without a blocker.
| Category | Free Option | Paid Upgrade | Why It’s Great |
|---|---|---|---|
| VPN | Windscribe Free | ExpressVPN | Generous free tier & user-friendly apps vs blazing speed worldwide servers and 24/7 support. |
| Password Manager | Bitwarden Free | 1Password | Open-source security & multi-device sync vs seamless UI, family sharing, and watchtower alerts. |
| Browser Security | HTTPS Everywhere | uBlock Origin | Auto-upgrades all sites to HTTPS vs advanced ad-&-tracker blocking with minimal performance hit. |
These tools cover the critical layers of your travel tech stack—encrypting your tunnel, securing credentials, and hardening your browser—to keep you connected and protected wherever you roam.
Next Steps
Let’s wrap up and keep you one step ahead on every trip.
| Security Layer | Adoption Rate |
|---|---|
| VPN Usage (Global) | 31 % of internet users rely on a VPN to secure public WiFi connections |
| Two-Factor Authentication | 57 % of medium-sized businesses and growing in personal use |
| Built-In VPN Routers | 67 % of top portable travel routers offer integrated VPN support |
Recap of Key Takeaways
- VPN first – Encrypt every connection with a no-logs VPN and kill switch.
- Enable 2FA – Lock down your most sensitive accounts (email, banking, VPN) with multi-factor authentication.
- Plan backups – Carry a portable router or power-bank hotspot and use vetted café loyalty networks when needed.
Stay Informed & Connected
- Subscribe to our quarterly Travel Security Updates for the latest tips, threat alerts, and tool reviews.
- Share this guide with fellow travelers to help them stay safe on public WiFi.
to print, pin, or save on your device—your ultimate companion for secure connections on the go.
Conclusion
Public WiFi doesn’t have to be a digital minefield. By layering defenses—starting with a trustworthy VPN, bolstered by browser privacy extensions and two-factor authentication—you build a fortress around your data. Pre-travel preparation ensures your software is patched, passwords are unique, and your toolkit includes a password manager and VPN app.
On the road, recognize red-flag networks by their generic SSIDs or overreaching captive portals, and lean on alternative connections like mobile hotspots, local eSIMs, or offline-first apps when needed. Should your primary link falter, emergency solutions—travel routers with built-in VPNs or power-bank hotspots—keep you connected without compromise.
Top tools like ExpressVPN, Bitwarden, and uBlock Origin automate protection layers. Finally, embed these practices into your routine: download our complete “Public WiFi Safety Toolkit,” subscribe for quarterly security updates, and share these tips with fellow travelers. With vigilance and the right gear, you’ll surf securely anywhere in the world.
FAQs
What is the biggest risk of using public WiFi?
The greatest danger is a “man-in-the-middle” attack, where hackers intercept data—like passwords and financial info—as it travels between your device and the hotspot.
Do I really need a VPN on public WiFi?
Yes. A reputable VPN encrypts all traffic, preventing eavesdroppers and rogue hotspots from harvesting your data.
Can I enable two-factor authentication on any account?
Most services—email, banking, social media, and VPNs—offer 2FA. Use an authenticator app for higher security than SMS codes.
What if I forget to update my software before traveling?
Unpatched apps and OS vulnerabilities are prime targets. Always enable automatic updates or manually patch before departure.
Are travel routers worth the investment?
If you frequently rely on untrusted networks, a travel router with built-in VPN offers a private, encrypted access point—even from a hotel ethernet jack.




















